Load balancer
- Increase capacity of application server by distribute traffic to multiple instances
- Reliability of applications
- Generally grouped into 2 categories: Layer 4 and Layer 7
- Layer 4 is transport layer LB include protocols like TCP, IP, UDP, FTP
- Layer 7 is application layer LB include protocol like HTTP/s
- Server side LB like HAProxy, Nginx offer centralized load balancer where these server act like reverse proxy and LB traffic to destination application server.
- Client side LB like Ribbon offer load balancing from client end itself with help of service discovery tools (Zookeeper, Etcd, consul etc.)
- Both type of LB their own pros and con.
- In Nuclei we are using Layer 7 LB for gRPC with Envoy proxy. It is also act like client side load balancer. In Kubernetes, application and envoy proxy container reside into same pod and intercept all incoming and outgoing requests.
- Why Envoy proxy? It is providing out of the box solution e.g. security, load balancing and traffic management, observability. Hence, application code need not to worry about all these thing.
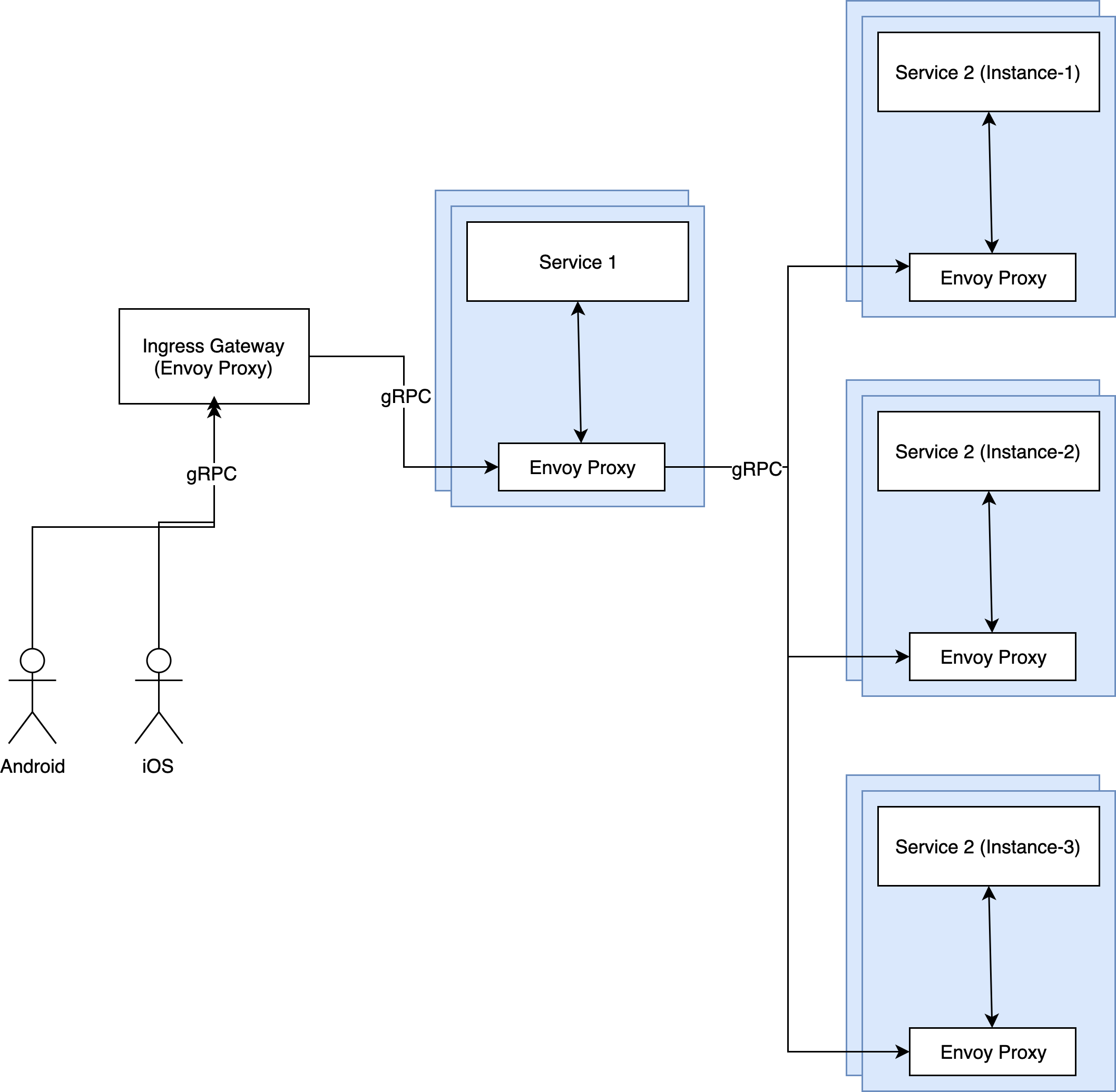
Ingress Gateway
In micro service architecture there are three type of communication happening.
- Ingress: Traffic coming to cluster referred as Ingress. In case of Nuclei, Android/iOS call to server
- **Service-to-service: **one service call other service. In case of Nuclei, Recharge service calling to Checkout services (Cart, Order, Payment, Coupons etc.)
- **Egress: **Traffic going outside to cluster referred as Egress. (In case of Nuclei, services used to call third-party vendor/services (ClearTrip, Redbus etc.)
It is important to protect all services from outside world, and expose only those services which will be called from Android/iOS client rest service should be blocked by default. We are using Istio service mesh, having concept of VirtualService which help us to expose limited set of service to outside world.
Configuring ingress gateway for gRPC is little tricky. Lets see some example:
- Package in proto file is important in above service package name is com.gonuclei.grpc
- Create a Ingress Gateway, and assign VirtualService
- In virtual service, we are allowing package prefix to call from outside cluster.
- It will be block other requests, only allow services having package com.gonuclei.grpc